Iranian State Hackers Target Defense Organizations With Password Spray Attacks: Microsoft

Sep 15: Iranian nation-state threat actor Peach Sandstorm (HOLMIUM) has been using password spray attacks to gain access to thousands of organizations in the satellite, defense, and pharmaceutical sectors around the globe.
Password spraying is a technique where threat actors attempt to authenticate to many different accounts using a single password or a list of commonly used passwords.
Between February and July 2023, Peach Sandstorm carried out a wave of password spray attacks against thousands of environments. By attempting to authenticate to a large number of accounts with a small number of passwords, Peach Sandstorm is able to increase its chances of success while minimizing the likelihood of automatic account lockouts.
Microsoft observed Peach Sandstorm using two distinct sets of TTPs in the early stages of the intrusion lifecycle in 2023 attacks. In later stages of known compromises, the threat actor used different combinations from a set of known TTPs to drop additional tools, move laterally, and ultimately exfiltrate data from a target.
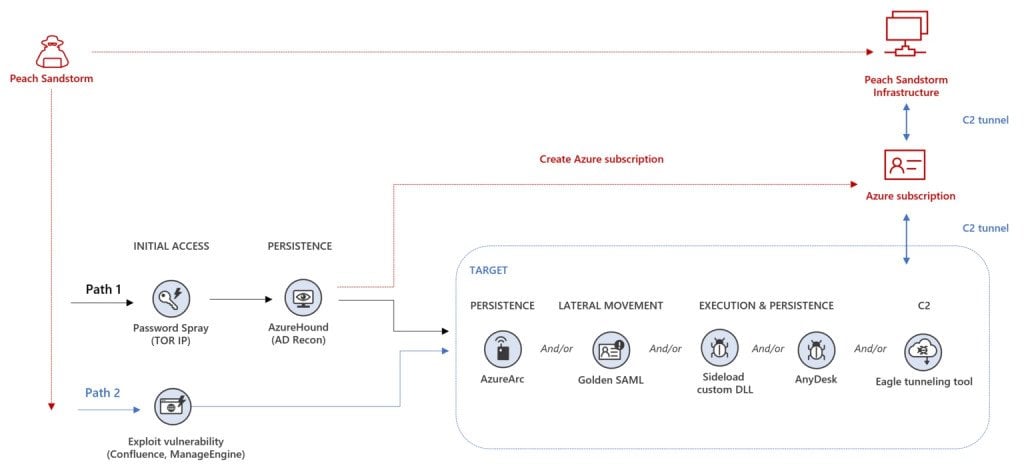
Once Peach Sandstorm has gained access to a victim’s account, they can use it to move laterally through the organization and collect sensitive information. This information could include customer data, intellectual property, or military secrets.
Peach Sandstorm is an Iranian nation-state group known to target organizations in multiple countries. In past attacks, Peach Sandstorm has pursued targets in the aviation, construction, defense, education, energy, financial services, healthcare, government, satellite, and telecommunications sectors.
[Originally published on: Iranian State Hackers Target Defense Organizations With Password Spray Attacks: Microsoft (abijita.com)]






Leave Comment